Cloudflare disclosed an incident in which a North Korean spy infiltrated a client company, emphasizing that South Korean businesses must be prepared for insider threats.
Michael Tremante, Cloudflare’s Senior Director of Application Security and Product, revealed the infiltration process during a press briefing on Tuesday at the Josun Palace in Gangnam, Seoul. He stated that there was an actual instance where a client hired a North Korean spy.
Tremante explained that an individual who had gone through the usual hiring process for an artificial intelligence (AI) company turned out to be a North Korean spy. He further noted that even though they passed the resume screening, it failed to detect the anomaly early enough, which allowed the spy to start working.
He continued that this individual exhibited behavior significantly different from that of regular employees, such as downloading an unusually large amount of data immediately after connecting to the virtual private network (VPN). Further noting that after reviewing their peculiar behavior and resume, it confirmed they were a spy and terminated their employment two months later.
Tremante underscored the seriousness of the situation by noting that there have been numerous cases where individuals presumed to be allies or internal staff turned out to be adversaries.


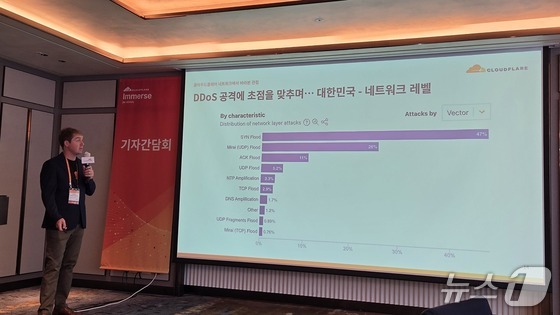
Jo Won-kyun, the head of Cloudflare’s Korean branch, speaks at a press conference / Provided by Cloudflare
@@@
