A North Korean-backed hacking group has set its sights on Google Android mobile devices. The hackers have been remotely wiping smartphones and tablets, deleting data without authorization.
On Monday, the Genians Security Center released a report detailing, Remote Reset Tactics Targeting Android Devices.
The attack campaign in question has been dubbed Konni. It is believed to be associated with North Korea’s Reconnaissance General Bureau and the Kimsuky group, also known as Advanced Persistent Threat (APT) 37.
The Konni campaign initially infiltrated targets using spear-phishing tactics. They sent targeted phishing emails to specific individuals within organizations. Masquerading as the National Tax Service, they attached malicious files disguised as requests for tax evasion documentation.
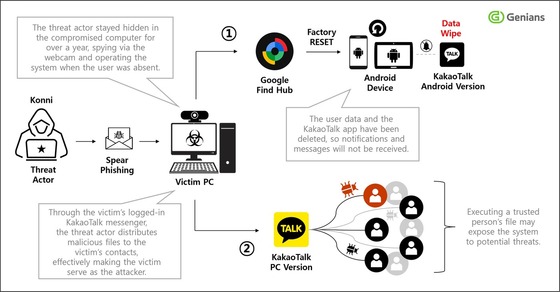
Opening these email attachments allows hackers to seize control of the victim’s personal computer (PC). Among the victims was a specialized psychological counselor for North Korean defector youth. The attackers used the counselor’s PC as a launchpad for widespread attacks on mobile devices.
On September 5, hackers sent a malicious file titled, Stress Relief Program, via KakaoTalk to a North Korean defector student. This led to further infections on additional devices. On September 15, the distribution of malicious files was confirmed through another victim’s KakaoTalk account.
A representative from Genians explained that this is a classic social engineering attack that precisely targets the psychological and social context of the victim using trust-based communication.
Specifically, the attackers employed a dual tactic of remote device reset and personal data deletion to block the victim’s awareness of the attack.
They exploited Google’s Find My Device feature, typically used for tracking lost or stolen devices. By gaining remote control access through compromised Google accounts, they also tracked the victim’s real-time location (GPS coordinates).
The representative stated that they particularly targeted victims when they were away from their devices, making it difficult for them to receive important messages and notifications, thereby conducting prolonged attacks.
They added that this is the first known instance where a state-backed campaign has exploited Google’s device tracking feature.
This incident clearly demonstrates that state-sponsored cyberattacks can target not only PCs but also mobile devices in everyday life. The center recommended strengthening monitoring through endpoint detection and response (EDR) solutions as a countermeasure.
Additionally, the center urged service providers like Google to implement additional verification procedures to confirm the true ownership of mobile devices. Biometric authentication such as facial recognition and fingerprint scanning, along with PIN entry, could serve as alternatives. The center also stressed that messenger platforms should enhance security checks for file sharing.
