
A recent report titled, APT Down: The North Korea Files, published by the U.S. hacking magazine Phrack, warns that the recent surge in cyber attacks not only threatens telecommunications companies and businesses but also indicates a breach of South Korean government systems.
The report suggests that the North Korean hacking group Kimsuky, operating under Pyongyang’s Reconnaissance General Bureau, has been persistently targeting South Korea’s Ministry of the Interior and Safety, Ministry of Foreign Affairs, Defense Security Command, and major telecom providers.
Equally alarming is an analysis from Korea University’s Graduate School of Information Security, which raises the possibility that a Chinese group rather than North Korea could be behind these sophisticated attacks.

Government Electronic Document System Compromised: Classified Information from Key Ministries Exposed
On Friday, information technology (IT) and cybersecurity experts reported that the U.S. non-profit organization DDoSecrets released a trove of data titled, APT Down – The North Korea Files on August 8.
This cache, approximately 8.9GB in size, contains data exfiltrated from workstations and Virtual Private Servers (VPS) believed to belong to a state-sponsored hacker known as KIM. The information was obtained by white-hat hackers operating under the aliases Saber and cyb0rg, and was first disclosed in Phrack’s 40th-anniversary edition.
The report reveals that the attackers infiltrated Onnara, the government’s integrated electronic document system, and extracted about 2,800 logs related to public officials’ Government Public Key Infrastructure (GPKI) signatures.
Specifically, the compromised data includes: △ authentication records and password decryption Java programs from the internal networks of the Ministry of Unification and the Ministry of Oceans and Fisheries △ administrative electronic signature certificates from the Ministry of the Interior and Safety △ source code from the Foreign Ministry’s internal Kkaebi Mail server.
The Onnara system serves as the backbone for document creation, review, and approval across all government departments. It houses not only official documents but also emails, video conference materials, and schedules for cabinet meetings and ministerial activities.
Suspicions of a breach at KT, a major South Korean telecom, emerged after the Phrack report uncovered evidence of secure sockets layer (SSL) key leaks. This revelation was followed by a series of minor payment system breaches. Investigators are still determining whether there is a connection between the government hacking incident and these payment system intrusions.
Researchers from Korea University’s Graduate School of Information Security posit that the hackers targeting the government may be linked to Chinese-backed groups such as APT41 and UNC3887. This assessment is based on observed patterns, including adherence to Chinese public holidays and access to the Chinese video platform AcFun.
Sources indicate that the National Intelligence Service was aware of the hack before the Phrack report became public and had already issued directives to the affected departments.
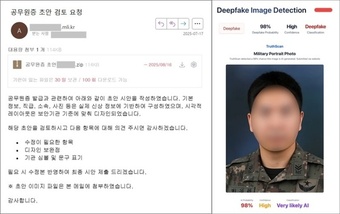
North Korean Kimsuky Group Leverages ChatGPT to Create Counterfeit Military IDs for Spear-Phishing Campaigns
The Kimsuky group continues to employ generative artificial intelligence (AI) tools, including ChatGPT, to produce fake military identification cards for use in targeted spear-phishing attacks.
A July report from the Genius Security Center noted that while ChatGPT typically refuses requests to create fraudulent identifications (IDs), the group appears to be using advanced jailbreak techniques by manipulating command prompts and persona settings to bypass these safeguards.
The National Intelligence Resource Management Institute reports a staggering 100.1% year-over-year increase in hacking attempts on central government agencies, totaling 161,208 incidents last year. Notably, 22.2% of these attempts focused on system privilege acquisition.
Analysts point to an alarming trend of increasingly complex attacks aimed at establishing long-term system control, moving beyond simple data theft for financial gain.
Professor Kim Seung-joo from Korea University’s Graduate School of Information Security issued a stark warning: The network separation policy that has been a cornerstone of cybersecurity for South Korea’s financial and public institutions was severely compromised by the shift to remote work during the COVID-19 pandemic. Further noting that if the current administration’s AI for Everyone initiative is implemented without addressing these vulnerabilities, it could face even more severe security breaches.
He advised that the government should conduct a comprehensive security audit to identify and rectify all existing vulnerabilities before proceeding with any large-scale AI implementation.



