
On October 17, Google’s Threat Intelligence Group (GTIG) disclosed that they had uncovered evidence of a North Korean-affiliated hacking group, known as UNC5342, employing a novel blockchain-based attack method to pilfer cryptocurrencies and gather sensitive information.
GTIG’s report detailed that UNC5342 exploited a cutting-edge malware concealment technique dubbed EtherHiding. This method repurposes public blockchains as command and control channels. The report explains that EtherHiding stores and disseminates malicious payloads through decentralized blockchain networks, rather than conventional centralized servers. This approach renders the command delivery routes virtually impervious to blockades and makes tracing nearly impossible.
The report emphasizes that this marks the first documented instance of such sophisticated technology being deployed by state-sponsored cyber operatives.
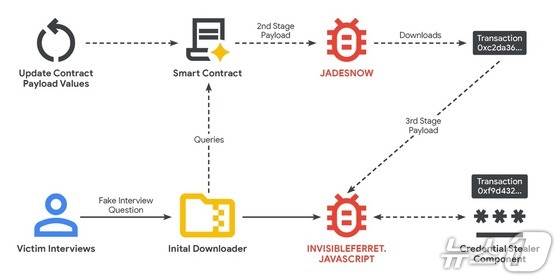
GTIG’s analysis reveals that UNC5342 executed a social engineering campaign, christened Contagious Interview by Palo Alto Networks, to dupe developers into unwittingly installing malware.
The attack vector compromised victims’ systems through an intricate, multi-stage infection process, targeting a range of operating systems including Windows, macOS, and Linux.
The hackers ingeniously stored malicious command codes on immutable blockchain ledgers, accessing them in read-only mode to maintain persistent, anonymous remote control. They adeptly circumvented security measures by dynamically swapping out payloads as needed.
GTIG’s assessment concludes that this case demonstrates UNC5342’s capability to effectively neutralize blocking attempts through EtherHiding, enabling them to sustain prolonged cyber offensives.
Robert Wallace, who heads Google Cloud’s Mandiant Consulting division, warns that state-sponsored hacking groups are leveraging increasingly adaptable malware to outmaneuver law enforcement responses. He underscores that this development signals an escalating complexity and intensity in the cybersecurity threat landscape.
