
There is an organization that seems to ramp up its activity when inter-Korean relations deteriorate: North Korea’s cyber hacking unit. While most people tend to overlook the immediate impacts, these hackers are increasingly encroaching on our daily lives. Reports indicate that since last year, North Korean hacking groups have been repeatedly targeting public institutions, semiconductor equipment manufacturers, defense contractors, courts, drone companies, and telecommunications firms.
North Korea has long attempted hacking across various sectors. Among these efforts, cyber intrusions aimed at South Korean military networks hit an all-time high in the first half of this year. According to the Korea Cyber Operations Command, North Korean attempts to hack South Korean military systems increased by 44.7% in the first six months of this year compared to the same period last year.
On October 2, just before the Chuseok holiday, I met with Moon Jong-hyun, an expert on North Korean cyber threats, at Genians headquarters in Anyang, Gyeonggi Province. He stated that while North Korea’s hacking capabilities are ranked third or fourth globally, the standards vary depending on the target. When South Korea is the target, North Korea can be considered the most formidable cyber sniper compared to any other country.
Although the international community views North Korea as a country with low economic power and information technology (IT) capabilities, in the realm of cyber hacking targeting South Korea, they understand the culture and language best, which significantly increases their infiltration capabilities and threat levels in people’s daily lives.
North Korea now appears to be aiming not just to extract information sporadically but to lie dormant in cyberspace, planning to exert decisive influence on reality during critical moments. This is why we need to maintain a broad view of their specialized and sophisticated operations and develop long-term countermeasures.
North Korean Hacking: Sophisticated Threats Realized through Remote Coercion
If North Korean hackers planned to assassinate a high-value target in South Korea without face-to-face contact, what methods might they employ?
Moon has been researching North Korean cyberattacks since 2001. He has served as an advisor to various government agencies, including the National Cyber Security Center (NCSC), the Korea Internet & Security Agency (KISA), the National Police Agency, the Military Counterintelligence Command, the Cyber Operations Command, the Ground Operations Command, and the Ministry of Foreign Affairs. He identified software-based assassination as the worst-case scenario that North Korea could potentially execute. To carry this out, hackers would first need to understand the target’s operational patterns and schedule through long-term surveillance enabled by hacking. By compromising information about individuals in the target’s orbit, they could apply pressure and potentially execute their objectives through these unwitting accomplices. This hypothetical scenario is alarmingly close to what North Korea’s current hacking capabilities can achieve. The potential for this to escalate beyond mere information theft into physical and diplomatic security issues is significant.
He noted that cyberspace is no longer limited to stealing personal information from computers. It’s approaching a stage where identifying and exploiting personal vulnerabilities could force individuals to carry out orders, potentially putting anyone in life-threatening situations. While physical harm can be inflicted through conventional weapons, it now faces the emergence of software killers.
Similar cases have already occurred. In April 2022, a South Korean army captain was indicted for leaking military secrets after allegedly receiving about 48 million KRW (approximately 33,600 USD) in Bitcoin from a suspected North Korean operative. Reports suggest that the captain’s vulnerability stemmed from financial difficulties due to gambling debts. North Korean hackers likely gathered extensive personal information beforehand, including details about the acquaintance who first introduced him to the North Korean contact, enabling a targeted approach.
He stated that attacks that can directly threaten lives remotely are increasingly becoming a reality. With critical infrastructure like autonomous driving systems, traffic signal controllers, and robotic surgery equipment being controlled by software and networks, North Korean cyberattacks that disrupt or cause these systems to malfunction could lead to immediate physical harm and casualties.
Moon emphasized that attacks targeting industrial control systems and ransomware incidents in the medical and energy sectors demonstrate that these threats are not hypothetical. He said that as cyberspace’s influence expands into the physical world, sectors with weak security become prime targets. Establishing robust early detection and response (EDR) systems for abnormal behavior, and strengthening public-private partnerships for cyber threat intelligence sharing, are now crucial.
Deepfake and AI Integration: Evolving into Long-Term Ambush Strategies
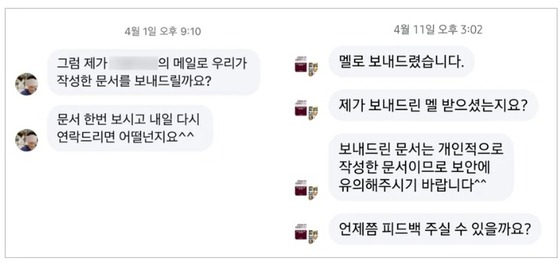
North Korean hackers invest considerable effort in accessing high-value targets. According to a threat analysis report from the Genieus Security Center (GSC), North Korean hacking groups employed sophisticated infiltration strategies targeting defense and North Korea-related activists through platforms like Facebook and Telegram from March to April. During this period, hackers reportedly used two Facebook accounts to scout and explore potential targets.
Once they identified a target, they typically initiated contact through friend requests or direct messages. They then shared document files with titles related to the recipient’s field of work, sending malicious bait files to lure them into executing hidden malware. Profile pictures were carefully chosen to appear as ordinary South Korean citizens. This method aims to build rapport through conversation, lowering the target’s guard and encouraging them to open the malicious file.
Late last year, a case emerged where malicious files were spread through KakaoTalk, South Korea’s most popular messaging app. Files distributed in group chats included an HWP document (a common Korean file format) and an LNK shortcut file hidden in a ZIP archive. The North Korean operatives first infiltrated individual devices, then patiently waited before cleverly distributing malicious files across multiple chat rooms with calculated time delays. They exploited the trust people place in files sent by familiar contacts.
Moon said that they meticulously build trust and establish rapport before launching sustained attacks. Some victims have been unknowingly compromised for over a year, subjected to surveillance through webcams or remote access tools. Others face repeated hacking attempts until the attackers succeed. This persistent, long-term operation is known as an Advanced Persistent Threat (APT), and it’s becoming increasingly sophisticated. While they still rely heavily on human operatives, the integration of artificial intelligence will likely usher in an even more dangerous era. The recent renaming of North Korea’s reconnaissance bureau to the Reconnaissance Information Bureau signals a clear shift in their strategy.
The South Korean government reported that North Korea reorganized its Reconnaissance Bureau, responsible for gathering intelligence on South Korea and overseas targets, into the Reconnaissance Information Bureau on September 15. This change likely aims to enhance their capabilities for acquiring and analyzing external information, especially as North Korea prepares to operate military reconnaissance satellites starting in November 2023.
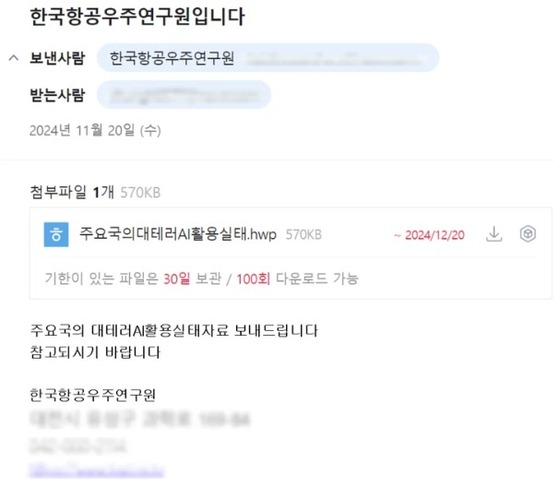
In a recent development, North Korea was caught attempting to hack South Korean military institutions by forging fake identification cards using generative artificial intelligence (AI). The attackers sent emails with the subject line Request for ID Issuance Review, attaching malicious files that displayed convincing fake military personnel identification (ID) images.
Analysts believe they created these deepfake images using generative AI tools like ChatGPT, combined with a relentless APT attack strategy involving repeated email attempts until the malware is executed.
Moon explained that North Korea’s cyber operatives have accumulated years of experience, significantly refining their attack range and sophistication. When combined with AI, their capabilities will see a dramatic boost. He added that it’s as if they’ve developed a comprehensive curriculum, systematically learning what information to gather, how to conduct reconnaissance, and how to execute attacks in a step-by-step manner.
The hackers are reportedly investing consistent time and resources into complex supply chain attacks. For instance, they may compromise the servers of reputable software companies to implant malware into program codes under development. This approach allows them to set long-term traps, enabling them to secure critical information at opportune moments.
Even ordinary individuals can become targets. There have been frequent incidents of personal information being hacked from students at prestigious universities. Moon speculates that North Korean operatives view this as a long-term investment, anticipating that these individuals may hold significant positions in South Korean society in the future. The value of such information can change dramatically over time, depending on geopolitical circumstances.

Need to Recognize that Cybersecurity Professionals Form a Critical Part of the National Security Infrastructure, Much Like Other Essential Services
However, even when there are suspicious circumstances indicating a North Korean hacker attack, reports of such incidents are rare. Most people tend to delete suspicious emails or social media messages and quickly forget about them.
Moon noted that victims often exhibit a tendency to dismiss their suspicions and try to resolve issues on their own, which is a dangerous characteristic when dealing with state-sponsored cybercrimes.
Consequently, both private companies and government agencies cannot rely solely on voluntary reports. Experts utilize various community-based Open Source Intelligence (OSINT) platforms to filter and analyze hacking-related attack data. They also share threat information with relevant agencies and identify new threats through their own security systems equipped with advanced sensors.
Some security experts conduct in-depth interviews with victims to gain unique insights and actively collect information. In such cases, it may be necessary to trace hackers’ digital footprints or thoroughly investigate the systems of hacking victims.
Determining how a hack was conducted and identifying who was behind it are fundamentally different challenges. While law enforcement can apprehend suspects, attributing cyberattacks to specific nation-states requires a level of expertise akin to forensic analysis. Identifying whether the perpetrators are from China, North Korea, or Russia demands years of specialized experience. Unfortunately, there’s a shortage of individuals with this depth of knowledge in the field.
In reality, few experts can conclusively identify the perpetrators behind sophisticated hacks. Moon stated that private security professionals mainly focus on analyzing hacking methods and attack processes. Uncovering the state actors behind hacking incidents requires continuous interest, effort, and unwavering determination from security experts. It hopes to see more collaboration among experts in identifying and attributing these threats in the future.”
