Intelligence analysts suggest that state actors from politically and security-sensitive nations such as North Korea or China may be behind the hacking groups targeting the South Korean government.
These threat actors primarily infiltrate the servers of key government agencies and corporations, implant malware, and exfiltrate data. Their operations may escalate beyond financial gain to pose significant national security risks or advance political agendas.
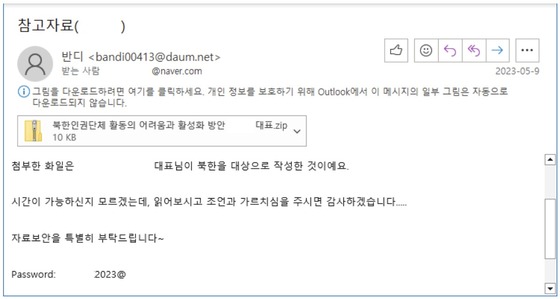
North Korean Spear Phishing Campaigns Utilize Malware-Laden Emails
On September 27, information technology (IT) and cybersecurity experts reported that the North Korean hacking group Kimsuky predominantly employs targeted spear phishing tactics against specific individuals or organizations.
Kimsuky is believed to be a state-sponsored cyber unit under North Korea’s Reconnaissance General Bureau. The group has expanded its operations beyond South Korea to target Western nations, including the U.S., gathering sensitive diplomatic and defense intelligence for the North Korean regime.
Spear phishing is a sophisticated cyber attack method targeting specific entities such as government departments or corporations. Attackers disseminate emails containing various types of malware disguised as legitimate Uniform Resource Locators (URLs), Korean Microsoft Office documents, or Windows PowerShell scripts, luring targets to phishing sites to steal sensitive information.
A report on North Korean hacking trends published in the cybersecurity magazine Phrack revealed that attackers, likely Kimsuky, breached the South Korean government’s integrated electronic document system Onnara and exfiltrated public officials’ digital signature (GPKI) verification logs.
The report identified a Go-language malware called Troll Stealer that is capable of extracting GPKI certificates and keys from infected devices. Investigators found thousands of files containing Troll Stealer on the attackers’ workstations.
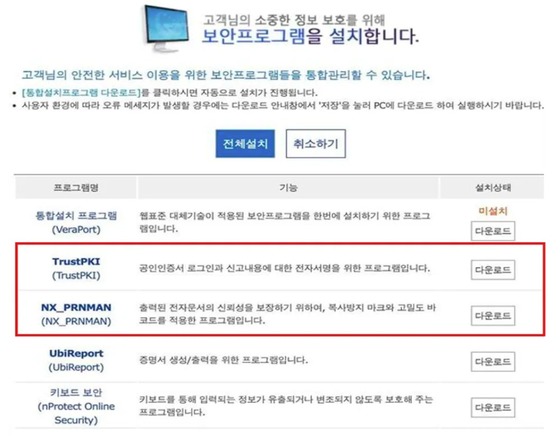
Troll Stealer was distributed through security program download pages that activated when accessing specific domestic websites, masquerading as installation files TrustPKI and NX_PRNMAN to infiltrate servers.
Last year, U.S.-based cybersecurity firm Zscaler uncovered a new Google Chrome extension named Translatext, developed by Kimsuky. This malicious extension can bypass the security measures of popular South Korean email providers like Naver, Kakao, and Gmail to steal user information.
The extension operates by displaying a phishing site after accessing the portal login page, prompting users to input their credentials, which are then captured by the attackers.
Zscaler noted that Kimsuky briefly uploaded this program to their GitHub account on March 7 last year, only to remove it the following day. Analysts interpret this as an attempt to minimize exposure while targeting specific individuals for short-term malware deployment.
Chinese Hackers Employ Stealthy Tactics for DNS Reconnaissance and Firewall Evasion
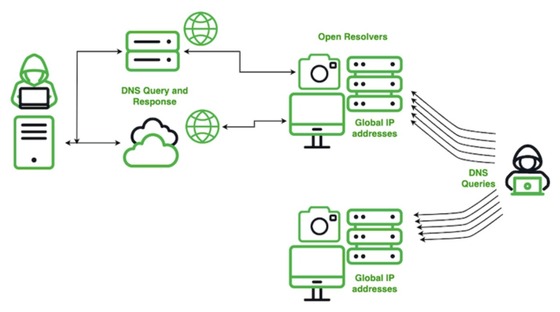
The Chinese hacking group SecShow has been observed conducting domain name system (DNS) reconnaissance to establish environments conducive to distributed denial-of-service (DDoS) attacks.
SecShow is a China-based hacking organization believed to be affiliated with the country’s education and research networks, tasked with collecting global cybersecurity data.
DNS enables website access using human-readable domain names instead of numerical internet protocol (IP) addresses. SecShow operates within the China Education and Research Network (CERNET), conducting worldwide DNS exploration.
U.S. cybersecurity firm Infoblox reported that although SecShow’s ultimate objectives remain unclear, the intelligence gathered could potentially be leveraged for malicious activities, solely benefiting the attackers.
Chinese hacking groups are also known for utilizing BPFdoor malware, which operates covertly to evade detection.
BPFdoor is a Linux-based backdoor that exploits the Berkeley Packet Filter (BPF) to stealthily exfiltrate server data while evading security solutions. This malware was confirmed to have compromised the subscriber authentication server (HSS) during the SK Telecom breach in April.



